Businesses need written policies and procedures, and there are five components to consider when creating and maintaining them.
These principles apply to all areas of business management and are especially important for the complex areas of cybersecurity, privacy, and information governance.
The legal significance of policies
A company”™s internal rules should include written documents and those documents might be called a policy, standard, procedure or something else. They need to comply with external laws and regulations and would be among the first documents demanded in a lawsuit or regulatory inquiry.
These policies are important for compliance purposes and as a management tool. Policies should never be just for show, nor sit unused on a shelf and we discuss their legal significance further in this prior article.
From a compliance view the Three Platforms to Connect model illustrates the optimal alignment of law (external rules) with internal rules (policies and procedures) and practice (what the organization does).

Compliance is a meaningful pursuit for attorneys and compliance officers, but other members of an organization will focus on revenue. Polices help with that too.
Business is more than compliance
Business is about fulfilling the mission, generating revenue, and serving customers and clients. Good businesses comply with laws, but no business exists solely to comply.
Policies are a management tool that help organizations fulfil their mission. Therefore, when we build our policies, they need to incorporate business objectives.
For this, we need a fourth platform which we want to align with the prior three, and we can show them in row like this.
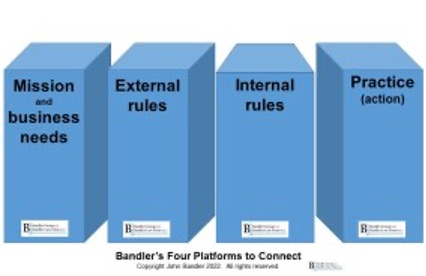
Other configurations can also be helpful to illustrate different concepts, including how the organization might have separate compliance functions and business functions, but they all go through the same platforms for internal rules and practice.
We need one final component, and that makes five
We need one more component to effectively create and maintain our internal rules ”“guidance.
Guidance is everywhere and this article is guidance. Information that organizations can choose to follow and adapt to their needs. Guidance helps us understand the laws, best practices, or ways others have done it before so we do not have to reinvent the wheel.
Information governance, cybersecurity, and privacy can be complex, and there is a lot of excellent guidance out there, including as discussed here on cybersecurity frameworks.
In sum, the five things we need to consider to create and maintain good policies are:
- Internal rules and policies
- Mission and business needs
- External rules (laws and regulations)
- Practice
- Guidance (including frameworks).
We can illustrate these five components like this:
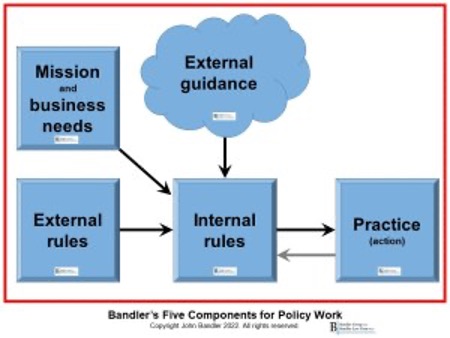
Organizations create their internal rules to achieve the mission, comply with laws, incorporate best practices, and to best direct the action of the organization and individuals within it. Not every rule needs to be written, but most organizations will need some degree of formality and documentation.
If there is a sixth component to be found, I have not come across it yet.
Cybersecurity means considering mission
When we put cybersecurity in the context of achieving business goals and good management of information assets, we realize it is more of a business and management imperative and less a dreaded chore.
Even if some do not appreciate the risks from criminals or believe “this will never happen to us”, all can appreciate that a comprehensive review of cybersecurity and information assets can yield technology efficiencies, marketing benefits, and security too.
For example, an organization might have social media or other online accounts that became dormant and disused during organization changes or personnel turnover. Those accounts are a vector for cybercrime attacks but are also an opportunity for free marketing to further the mission. A review of information assets can fix cracks and yield efficiencies.
Conclusion
Policies and other internal rules are a part of good business management to ensure goals are met, for the long-term health of the organization, and to achieve the mission. They are not just a compliance chore. Good management principles should extend to governance of information assets, cybersecurity, and privacy. For more details on each of the five components see this page and the linked articles.






















