The intensity and speed at which you hit the keys on your computer says a lot about yourself.
Now new research at Pace University”™s Seidenberg School of Computer Science and Information Systems has found a scientific way to detect cheating when students take online exams. But the findings have broader implications in a world rife with hackers and cybercrime. The U.S. Department of Defense has a strong interest in the college”™s findings.
Through keystroke and stylometry biometrics, a software program that records a person”™s typing patterns and linguistic style, the key-logger application can remember the behavior of a test-taker. That way, those giving online tests can determine whether the person taking the exam is the person enrolled in the class.
Amar Gupta, dean of Seidenberg School of Computer Science and Information Systems, said the college is introducing keystroke and biometrics on a limited basis in the lab and slowly expanding it to online education.
For the first time, researchers at Pace will pilot this software in three online courses this fall. Two of them will be computer science, and the third has yet to be determined.
“As we have more and more information on computers and as you deal with more people, it”™s more of an anonymous world where you don”™t see people”™s identity,” Gupta said. “As we look at online education, we have to be sure the person on the other end is the student he or she claims to be. This is a mechanism to detect and validate information based on small sets of data a person puts in.”
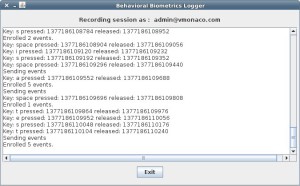
The research process requires collecting data from willing participants and finding a consistent variable to measure a user”™s behaviors on a keyboard, including length of time a key is pressed and released, the interval of time that passes between each key and the types of words used. One of the primary students involved in the research is John V. Monaco, a graduate student in computer science.
“We have 200 users on our database and we”™ve tracked each of their keystroke biometrics,” Monaco said. “After we collect their keystroke biometrics, we analyze it and figure out what data is useful and what isn”™t. Then we decide how to use the data to actually authenticate a user and give it a structure.”
Monaco has been researching keystroke and stylometry biometrics for more than two years as part of his master”™s thesis. While doing research, he realized this technology goes beyond the educational setting. The development of this application can potentially be used for any circumstances that require protecting a person”™s identity. He said this software application will provide higher levels of authentication that consistently monitors a person”™s actions beyond the login process.
“People generally use passwords that are easy to guess or reuse passwords for multiple accounts,” Monaco said. “So that creates a risk. Besides, once you get past the initial username and password authentication, there”™s nothing that continuously monitors your input to the computer after that.”
Charles Tappert, computer science professor and researcher at Pace, said Pace”™s biometrics research began in 2004 when he and professor Sung-Hyuk Cha started studying pervasive computing, pattern recognition and data mining and stumbled upon a program that collects keystroke information.
“There are two basic types of biometrics ”“ physiological and behavioral,” Tappert said. “We purposely chose to go into the less common biometrics of behavioral. We”™re one of the first universities to do work in this area.”
Over time, the government required schools to ensure that students don”™t cheat on online exams, Tappert said.
“In 2008, the government came up with the Higher Education Opportunity Act, which is basically saying institutions of higher learning like the universities should ensure that students taking online courses are the correct students registered for the course,” Tappert said.
The U.S. Defense Department has provided resources for Pace to do research and collect data on keystroke and stylometry biometrics. Researchers and program developers are aggregating their data and using their prototypes as models for a final product that can be marketed in corporations and government divisions, Gupta said.
Although keystroke and stylometry biometrics has proven to be reliable, the system isn”™t entirely fool proof, Monaco said.
“There are still factors we haven”™t accounted for, especially external factors that change a person”™s typing pattern or word choice, if this was going to be implemented on a large scale system,” Monaco said.
More information on Seidenberg’s information technology program can be found at:Â http://www.pace.edu/seidenberg/ms-in-information-systems




















Comments 1